There could be from one to over ten ports used within your MySQL ecosystem. It really depends on what you have enabled, which components you are using, how your applications connect, and other characteristics of your environment.
From a security point, these ports need to be opened just wide enough to allow the various components that should communicate to talk while blocking out anything else trying to hack its way in – the goal being to enforce the security principle of “least privilege”. Obviously, what you should not do is open everything to get things working, only to discover later you have left yourself entirely exposed and hacked. Don’t be “That Admin or DBA”.
Of course, how you block and open ports with proper ingress and egress rules depends on your environment – where you have various tools firewalls, VPNs, Operating Systems capabilities, etc. With some of our installation packages, our goal is to be secure by default as well as usability, and we will assist, but typically only for the most core ports. For example, the MySQL Windows installer will add rules to the Windows firewall, or the Linux packages add rules to SELinux or AppArmor.
However for less common, optional, or external product specific ports, we do not open them up for you in our packages, so you will need to do this yourself in those cases. With commands like the one for SELinux like
semanage port -a -t mysqld_port_t -p tcp <port open to mysqld>
Anyway, for this blog the goal is just port awareness, so I just wanted to list them out to make sure they are known and understood relative to
- What they are
- What uses them
- When they are used
- Is the communication encrypted by default (Yes in most cases)
- Limiting access
This reference applies to MySQL 5.7 and 8.0
Visually it looks something like this.
This is NOT a full reference – the tables below provide the full reference.
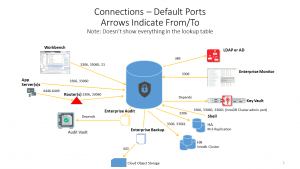
Or for all the details see
And a handy MySQL PORT quick reference table
MySQL Ports
| Technology | Default Port | SSL|Enc Def. | Required |
|---|---|---|---|
| Client - Server Connections (msql client, connectors, mysqldump, mysqlpump) |
|||
| MySQL Client to Server - MySQL Protocol – 3306 | 3306/tcp | Y | Y unless just using 33060 |
| MySQL Client to Server – New X Protocol – 33060 | 33060/tcp | Y | Y unless just using 3306 |
| MySQL Shell | |||
| MySQL Client to Server - MySQL Protocol – 3306 | 3306/tcp | Y | Y unless just using 33060 |
| MySQL Client to Server – New X Protocol – 33060 | 33060/tcp | Y | Y unless just using 3306 |
| For checks, from Shell to GR server during InnoDB cluster configuration. | 33061/tcp | Y | Y if running InnoDB Cluster |
| MySQL Workbench | |||
| MySQL Client to Server - MySQL Protocol – 3306 | 3306/tcp | Y | Optional - pick at least 1 |
| MySQL Client to Server – New X Protocol – 33060 | 33060/tcp | Y | Optional - pick at least 1 |
| Connects via SSH Tunnel | 22/tcp | Y | Optional - pick at least 1 |
| Client - Router Connections - | |||
| MySQL Client Any SQL to Router - MySQL Protocol | 6446/tcp | Inherited | Required if Router provides RW access |
| MySQL Client ReadOnly SQL to Router - MySQL Protocol | 6447/tcp | "" | Required if Router provides ReadOnly access |
| MySQL Router to Server - MySQL Protocol | 3306/tcp | "" | Required |
| MySQL Client Any API calls to Router – New X Protocol – 33060 | 6448/tcp | "" | Required if Router provides RW access |
| MySQL Client ReadOnly Calls to Router – New X Protocol – 33060 | 6449/tcp | "" | Required if Router provides ReadOnly access |
| MySQL Router to Server – New X Protocol – 33060 | 33060/tcp | "" | Required |
| High Availability | |||
| MySQL Group Replication internal communications port - 33061 | 33061/tcp | Y | Y |
| MySQL Replication | 3306/tcp | Y | Y |
| External Authentication * | |||
| MySQL Enterprise Authentication - LDAP * | 389/tcp | Y | Only if using External Authentication to LDAP. Also supports use of SASL |
| MySQL Enterprise Authentication - AD * | 389/tcp | Y | Only if using External Authentication to LDAP |
| Key Management (for TDE, Keyring Functions, etc) * | |||
| KMIP - used with Oracle Key Vault, Gemalto KeySecure, Thales Vormetric key management server, Fornetix Key Orchestration * | Varies, See key manager/vault specific documentation. | Y | Only required if TDE is using a KMIP server |
| Key Services - AWS KMS * | 443/tcp | Y | Only required if TDE is using AWS KMS |
| MEB backup | |||
| Communicate to Local Instance | 3306/tcp | Y | Optional - can connect with tcp|socket|pipe|memory |
| If Innodb Cluster/Group Replication | 3306/tcp | Y | Required for InnoDB Cluster Backup |
| Oracle Object Store | 443/tcp | Y | Optional |
| AWS S3 | 443/tcp | Y | Optional |
| Backup to Media Manager (SBT API) * | Varies - See backup media manager specific documentation | Vendor dependent | Optional |
So that’s my reference to MySQL Ports. I certainly hope its of value.
Thank you for using MySQL !