MySQL Enterprise Edition supports authentication methods that enable MySQL Server to use LDAP (Lightweight Directory Access Protocol), LDAP with Kerberos, or native Kerberos to authenticate MySQL users. MySQL Workbench 8.0.27 (and later) provides several connection methods that permit you to use LDAP and Kerberos authentication.
The server-side LDAP and Kerberos authentication plugins are included only in MySQL Enterprise Edition. These server-side plugins are not included in MySQL community distributions. The client-side plugins are included in all MySQL Workbench distributions, including community distributions. This enables users from any MySQL Workbench distribution to connect to a server that has the server-side plugin loaded.
Although MySQL Workbench includes the client-side plugins in all distributions, specific support for LDAP and Kerberos authentication is platform dependent. For example, authentication is not supported when MySQL Workbench is running on macOS.
This implementation of Kerberos authentication does not support MIT Kerberos on any platform.
The following table shows the platform support for each connection method.
Table 5.1 Connection Methods and Supported Platforms
| Connection Method | Windows | Linux | macOS |
|---|---|---|---|
| LDAP User/Password | Supported | Supported | Not supported |
| LDAP Sasl/Kerberos | Not supported | Supported | Not supported |
| Native Kerberos | Supported | Supported | Not supported |
In general, the following requirements must be satisfied to use LDAP or Kerberos pluggable authentication:
Server-side and client-side plugins need to be compatible, and the server-side plugin must be installed. To minimize the potential for incompatibilities, regularly upgrade the server and MySQL Workbench on a timely basis.
-
MySQL Enterprise Edition must be configured for the type of authentication protocol in use. Specific libraries, services, and servers that apply to each authentication method must be available to MySQL Server.
NoteMySQL Workbench restricts the use of SASL-based LDAP authentication to configurations using the Generic Security Service Application Program Interface (GSSAPI)/Kerberos authentication method. The exclusive use of SASL messages for secure transmission of credentials within the LDAP protocol is not supported.
-
A MySQL user account must be created or altered with syntax that specifies how the account authenticates. For example, to create an account for
skylarusing simple LDAP authentication (and the LDAP User/Password connection method), use a form of syntax similar to:CREATE USER 'skylar'@'localhost' IDENTIFIED WITH authentication_ldap_simple [BY 'LDAP user DN'];The
BYclause in this example indicates which LDAP entry the MySQL account authenticates against. Specific attributes of the distinguished name (DN) may vary depending on the LDAP server.
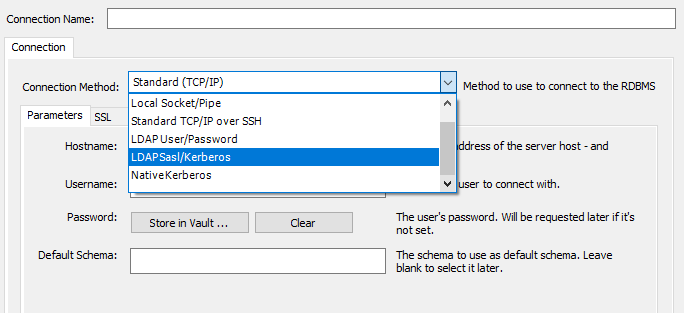
To set up the client-side connection from MySQL Workbench:
Click the manage connections icon (
 ) on the home screen to open the Manage
Server Connections dialog.
) on the home screen to open the Manage
Server Connections dialog.
-
From the Connection tab, select the LDAP User/Password, LDAP Sasl/Kerberos, or Native Kerberos connection method from the list.
With the server requirements satisfied, you can configure the parameters of the named connection from MySQL Workbench. The Section 5.3.4.1, “LDAP User/Password”, Section 5.3.4.2, “LDAP Sasl/Kerberos”, and Section 5.3.4.3, “Native Kerberos” sections identify the settings for each connection method.